前言
之前收到学姐送的Mac的时候还收到了一个Yubikey,最近在折腾完ZFS之类的之后终于有时间看看这个东西要怎么玩了。
什么是Yubikey呢?
这里引用一下官方的解释:
A YubiKey is a small hardware device that offers two-factor authentication with a simple touch of a button. YubiKeys are built strong enough for the largest enterprises, while remaining simple enough for anyone to use. The YubiKey NEO offers both contact (USB) and contactless (NFC, MIFARE) communications. YubiKeys can support FIDO U2F, Yubico-OTP, OATH-OTP, OATH-HOTP, OATH-TOTP, OpenPGP, and PIV, and one security key can support an unlimited number of applications without the need for drivers, client software, or batteries.
对于我来说的话我比较看中的是2FA和openpgp的支持,这篇文章也会着重讲解这两点,这篇文章算是drduh Yubikey Guide的中文版?
准备
这里要准备如下物品:
- Yubikey 我的是Yubikey 5NFC 的版本购买页面在官网
- 一台电脑(最好是Linux系统)
- 2个U盘 (一个作为Livecd环境制作GPG密钥,一个用于备份主密钥)
准备Livecd
之所以用livecd环境是为了保证安全,安装了gpg必要的软件之后可以断网不留痕迹。
这里用Ubuntu 2020 Desktop livecd为例子:
安装必要的软件,这里是用于yubikey的初始化,以及配置GPG密钥和LUKS所需要用到的工具,
下载ISO文件 (这个iso链接可能不可用,可以从Ubuntu官网下载这个最新的版本
1
| wget -c https://mirrors.aliyun.com/ubuntu-releases/20.10/ubuntu-20.10-desktop-amd64.iso
|
将U盘插入你的机器然后使用dd刻录安装介质
1
| sudo dd if=ubuntu-20.10-desktop-amd64.iso of=/dev/sdb bs=20M status=progress
|
耐心等待程序执行完成。
等到执行完成之后你就有了一个Ubuntu 20.10 Desktop的安装介质
livecd环境初始化
重启之后进入到机器的Boot Manger选择USB引导启动,进入Livecd环境。
连接网络之后安装必要的包:
1
| apt-get update && sudo apt install -y gnupg2 gnupg-agent gnupg-curl scdaemon pcscd
|
之后打开这篇文章,就可以断网了XDD
非livecd环境
如果你使用的是非Livecd环境,比如说Mac(像是我现在的操作就是在Mac上),你可以用Macports安装必要的包
1
| sudo port install gnupg2 pinentry-mac yubikey-manager
|
如果你在使用Gentoo,你可以使用以下命令:
1
| sudo emerge -av yubikey-manager app-crypt/ccid
|
开机启动pcscd服务:
1
2
| /etc/init.d/pcscd start
rc-update add pcscd default
|
添加用户到plugdev组
1
| sudo usermod -aG plugdev yafa
|
创建GPG KEY
创建临时工作目录
为了安全保障我们首先创建一个临时的工作目录:
1
| export GNUPGHOME=$(mktemp -d)
|
之后GPG KEY文件也会存放在这个目录下。
GPG 配置文件
进入我们创建的临时目录:
下载一个已经配置好配置文件:
1
| wget -O $GNUPGHOME/gpg.conf https://raw.githubusercontent.com/drduh/config/master/gpg.conf
|
生成Master Key
首先我们要生成的密钥是Master密钥,这个密钥仅用于认证:加密、签名、身份验证的子密钥。
安全提示:主密钥应该始终保持离线的状态,最好是只用来撤销或者是发布新的子密钥。子密钥应该只存在于Yubikey本身,确保不保留其他的副本。
使用GPG生成一个Master密钥,选择8个RSA仅用于认证功能,密钥为4096位(需要注意的是GPG 的Master Key不用设置过期,能够保持GPG Master Key不丢失就可以了,丢失了设置GPG Key延长日期并没有什么太大的用处。反而是管理子密钥不是很方便。):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
| gpg --expert --full-generate-key
gpg: keybox '/var/folders/8_/mkr2jpxx1pdgqx7jsnv04k100000gn/T/tmp.UdKeLYEs/pubring.kbx' created
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(9) ECC and ECC
(10) ECC (sign only)
(11) ECC (set your own capabilities)
(13) Existing key
(14) Existing key from card
Your selection? 8
Possible actions for a RSA key: Sign Certify Encrypt Authenticate
Current allowed actions: Sign Certify Encrypt
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? E
Possible actions for a RSA key: Sign Certify Encrypt Authenticate
Current allowed actions: Sign Certify
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? S
Possible actions for a RSA key: Sign Certify Encrypt Authenticate
Current allowed actions: Certify
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? Q
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (3072) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 0
Key does not expire at all
Is this correct? (y/N) y
|
输入你的姓名和邮件地址(comment可以写也可以不写):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
GnuPG needs to construct a user ID to identify your key.
Real name: Yafa Xena
Email address: i@yafa.moe
Comment: Freedom and responsibility
You selected this USER-ID:
"Yafa Xena (Freedom and responsibility) <i@yafa.moe>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: /var/folders/8_/mkr2jpxx1pdgqx7jsnv04k100000gn/T/tmp.UdKeLYEs/trustdb.gpg: trustdb created
gpg: key 0xBE5E83CAC35379C8 marked as ultimately trusted
gpg: directory '/var/folders/8_/mkr2jpxx1pdgqx7jsnv04k100000gn/T/tmp.UdKeLYEs/openpgp-revocs.d' created
gpg: revocation certificate stored as '/var/folders/8_/mkr2jpxx1pdgqx7jsnv04k100000gn/T/tmp.UdKeLYEs/openpgp-revocs.d/08A3150E30B49637D01C6C77BE5E83CAC35379C8.rev'
public and secret key created and signed.
pub rsa4096/0xBE5E83CAC35379C8 2021-03-14 [C]
Key fingerprint = 08A3 150E 30B4 9637 D01C 6C77 BE5E 83CA C353 79C8
uid Yafa Xena (Freedom and responsibility) <i@yafa.moe>
|
这里你输入Okay的时候会提示你给主密钥设置一个密码,需要重复输入两次,一定要记好你的这个密码。
将密钥的ID设置位环境变量,后面会用到:
1
| export KEYID=0xBE5E83CAC35379C8
|
添加子密钥
首先编辑主密钥用于添加子密钥:
1
2
3
4
5
6
7
8
9
10
11
| gpg --expert --edit-key $KEYID
Secret key is available.
gpg: checking the trustdb
gpg: marginals needed: 3 completes needed: 1 trust model: pgp
gpg: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1u
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
|
使用4096位RSA密钥。
子密钥的有效期为1年-可以使用离线主密钥续订这些子密钥。 请参阅轮转KEY。
签名密钥
使用addkey命令进行创建密钥,然后选择(4)RSA(仅签名),以创建签名密钥:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| gpg> addkey
Please select what kind of key you want:
(3) DSA (sign only)
(4) RSA (sign only)
(5) Elgamal (encrypt only)
(6) RSA (encrypt only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(10) ECC (sign only)
(11) ECC (set your own capabilities)
(12) ECC (encrypt only)
(13) Existing key
(14) Existing key from card
Your selection? 4
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (3072) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 1y
Key expires at Mon Mar 14 13:57:07 2022 CST
Is this correct? (y/N) y
Really create? (y/N) y
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
|
加密密钥
接下来,通过选择(6)RSA(仅加密)来创建加密密钥:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| gpg> addkey
Please select what kind of key you want:
(3) DSA (sign only)
(4) RSA (sign only)
(5) Elgamal (encrypt only)
(6) RSA (encrypt only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(10) ECC (sign only)
(11) ECC (set your own capabilities)
(12) ECC (encrypt only)
(13) Existing key
(14) Existing key from card
Your selection? 6
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (3072) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 1y
Key expires at Mon Mar 14 13:57:29 2022 CST
Is this correct? (y/N) y
Really create? (y/N) y
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
|
身份验证密钥
最后,创建一个身份验证密钥。
GPG不提供仅用于身份验证的密钥类型,因此选择(8)RSA(设置你自己的功能)并切换所需的功能,直到唯一允许的操作是Authenticate:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
| gpg> addkey
Please select what kind of key you want:
(3) DSA (sign only)
(4) RSA (sign only)
(5) Elgamal (encrypt only)
(6) RSA (encrypt only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(10) ECC (sign only)
(11) ECC (set your own capabilities)
(12) ECC (encrypt only)
(13) Existing key
(14) Existing key from card
Your selection? 8
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Sign Encrypt
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? S
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Encrypt
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? E
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions:
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? A
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Authenticate
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? Q
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (3072) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 1y
Key expires at Mon Mar 14 13:57:52 2022 CST
Is this correct? (y/N) y
Really create? (y/N) y
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
|
最后保存所做的操作:
验证
我们来看一下最终生成的密钥:
1
2
3
4
5
6
7
8
9
| gpg -K
/var/folders/8_/mkr2jpxx1pdgqx7jsnv04k100000gn/T/tmp.UdKeLYEs/pubring.kbx
-------------------------------------------------------------------------
sec rsa4096/0xBE5E83CAC35379C8 2021-03-14 [C]
Key fingerprint = 08A3 150E 30B4 9637 D01C 6C77 BE5E 83CA C353 79C8
uid [ultimate] Yafa Xena (Freedom and responsibility) <i@yafa.moe>
ssb rsa4096/0xD40C8A853177702B 2021-03-14 [S] [expires: 2022-03-14]
ssb rsa4096/0x80D9D0834E2A346E 2021-03-14 [E] [expires: 2022-03-14]
ssb rsa4096/0xD1144013D3F7F320 2021-03-14 [A] [expires: 2022-03-14]
|
导出KEY
导出时,主密钥和子密钥将使用你设置的密码进行加密。
保存密钥:
1
2
| gpg --armor --export-secret-keys $KEYID > $GNUPGHOME/mastersub.key
gpg --armor --export-secret-subkeys $KEYID > $GNUPGHOME/sub.key
|
创建吊销KEY
虽然尽可能去备份和保存主密钥,但是不排除丢失主密钥或者是备份失败的可能性(就像是这次安装Mac操作系统,最后发现备份U盘坏了。。。)。没有主密钥就没有办法更新或者是吊销子密钥,PGP的身份就毫无意义了。
更糟糕的事情是,没办法告诉别人自己的GPG密钥丢了可能被其他人利用起来了。唯一的办法就是吊销这个KEY。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| gpg --output $GNUPGHOME/revoke.asc --gen-revoke $KEYID
sec rsa4096/0xBE5E83CAC35379C8 2021-03-14 Yafa Xena (Freedom and responsibility) <i@yafa.moe>
Create a revocation certificate for this key? (y/N) y
Please select the reason for the revocation:
0 = No reason specified
1 = Key has been compromised
2 = Key is superseded
3 = Key is no longer used
Q = Cancel
(Probably you want to select 1 here)
Your decision? 1
Enter an optional description; end it with an empty line:
> Key has been compromised
>
Reason for revocation: Key has been compromised
Key has been compromised
Is this okay? (y/N) y
ASCII armored output forced.
Revocation certificate created.
Please move it to a medium which you can hide away; if Mallory gets
access to this certificate he can use it to make your key unusable.
It is smart to print this certificate and store it away, just in case
your media become unreadable. But have some caution: The print system of
your machine might store the data and make it available to others!
|
revoke.asc证书文件应存储(或打印)在安全位置,以防万一主备份失败时进行检索。
备份KEY
密钥一旦移动到YubiKey,就会从本地删除掉这个子钥!(也就是说一旦我们将子钥移动到了yubikey内,不使用yubikey就没办法对加密内容解密了) 创建密钥环的加密备份,并考虑使用密钥的纸质副本作为其他备份措施。
提示ext2文件系统(不加密)可以安装在Linux和OpenBSD上。 考虑改为使用FAT32 文件系统来实现MacOS / Linux/BSD/Windows平台的兼容性。
插入硬盘之后查看新添加的设备:
1
2
3
4
5
6
7
8
9
10
11
| sudo dmesg | tail
[692184.973943] usb-storage 2-8:1.0: USB Mass Storage device detected
[692184.974344] scsi host8: usb-storage 2-8:1.0
[692186.509922] scsi 8:0:0:0: Direct-Access Kingston DataTraveler 2.0 1.00 PQ: 0 ANSI: 4
[692186.510249] sd 8:0:0:0: Attached scsi generic sg3 type 0
[692186.510918] sd 8:0:0:0: [sdf] 15131636 512-byte logical blocks: (7.75 GB/7.21 GiB)
[692186.511628] sd 8:0:0:0: [sdf] Write Protect is off
[692186.511631] sd 8:0:0:0: [sdf] Mode Sense: 45 00 00 00
[692186.512625] sd 8:0:0:0: [sdf] Write cache: disabled, read cache: enabled, doesn't support DPO or FUA
[692186.525141] sdf: sdf1 sdf2
[692186.527842] sd 8:0:0:0: [sdf] Attached SCSI removable disk
|
用随机数写满整个硬盘:
1
| sudo dd if=/dev/urandom of=/dev/sdf bs=4M status=progress
|
这次我们要创建两个分区一个是加密存储GPG KEY,另外一个是存放公钥。
| 分区 | 文件系统 | 挂载点 | 大小 |
|---|
| /dev/sdf1 | LUKS | /mnt/gpg | 25M |
| /dev/sdf2 | fat32 | /mnt/public | 25M |
创建分区:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
| fdisk /dev/sdf
Welcome to fdisk (util-linux 2.36.1).
Changes will remain in memory only, until you decide to write them.
Be careful before using the write command.
Device does not contain a recognized partition table.
Created a new DOS disklabel with disk identifier 0xde306216.
Command (m for help): n
Partition type
p primary (0 primary, 0 extended, 4 free)
e extended (container for logical partitions)
Select (default p):
Using default response p.
Partition number (1-4, default 1):
First sector (2048-15131635, default 2048):
Last sector, +/-sectors or +/-size{K,M,G,T,P} (2048-15131635, default 15131635): +25M
Created a new partition 1 of type 'Linux' and of size 25 MiB.
Command (m for help): n
Partition type
p primary (1 primary, 0 extended, 3 free)
e extended (container for logical partitions)
Select (default p):
Using default response p.
Partition number (2-4, default 2):
First sector (53248-15131635, default 53248):
Last sector, +/-sectors or +/-size{K,M,G,T,P} (53248-15131635, default 15131635): +25M
Created a new partition 2 of type 'Linux' and of size 25 MiB.
Command (m for help): w
The partition table has been altered.
Calling ioctl() to re-read partition table.
Syncing disks.
|
初始化LUKS:
1
2
3
4
5
6
7
8
9
| cryptsetup luksFormat /dev/sdf1
WARNING!
========
This will overwrite data on /dev/sdf1 irrevocably.
Are you sure? (Type 'yes' in capital letters): YES
Enter passphrase for /dev/sdf1:
Verify passphrase:
|
打开LUKS分区:
1
| cryptsetup luksOpen /dev/sdf1 secret
|
初始化文件系统:
1
| sudo mkfs.ext2 /dev/mapper/secret -L gpg-$(date +%F)
|
创建挂载点:
1
| sudo mkdir /mnt/encrypted-storage
|
挂载分区:
1
| sudo mount /dev/mapper/secret /mnt/encrypted-storage
|
复制文件:
1
| sudo cp -avi $GNUPGHOME /mnt/encrypted-storage/
|
卸载分区和关闭LUKS:
1
2
| sudo umount /mnt/encrypted-storage/
sudo cryptsetup luksClose secret
|
导出公钥
重要提示如果没有公共密钥,您将无法使用GPG加密,解密或签名消息。 但是,您仍然可以使用YubiKey进行SSH身份验证。
现在我们要做的就是在可移动存储设备上创建另一个分区来存储公用密钥,之后可以连接网络并上传到密钥服务器。
首先初始化另外一个分区:
1
| sudo mkfs.ext2 /dev/sdf2
|
创建挂载点:
挂载分区:
1
| sudo mount /dev/mmcblk0p2 /mnt/public/
|
导出公钥到这个分区:
1
| gpg --armor --export $KEYID | sudo tee /mnt/public/gpg-$KEYID-$(date +%F).txt
|
上传到公开的keyserver:
这个默认的keyserver可以在gpg.conf配置文件中设置默认的,也可以像是这样手动指定:
1
2
3
| gpg --keyserver pgp.mit.edu --send-key $KEYID
gpg --keyserver keys.gnupg.net --send-key $KEYID
gpg --keyserver hkps://keyserver.ubuntu.com:443 --send-key $KEYID
|
配置Yubikey
插入YubiKey并使用GPG将其配置:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| gpg --card-edit
Reader ...........: Yubico YubiKey OTP FIDO CCID
Application ID ...: D2760001240103040006136541830000
Application type .: OpenPGP
Version ..........: 3.4
Manufacturer .....: Yubico
Serial number ....: 13654183
Name of cardholder: [not set]
Language prefs ...: [not set]
Salutation .......:
URL of public key : [not set]
Login data .......: [not set]
Signature PIN ....: not forced
Key attributes ...: rsa2048 rsa2048 rsa2048
Max. PIN lengths .: 127 127 127
PIN retry counter : 3 0 3
Signature counter : 0
KDF setting ......: off
Signature key ....: [none]
Encryption key....: [none]
Authentication key: [none]
General key info..: [none]
|
如果你的yubikey已经被锁住,或者是忘记密码被锁了,可以参考重置
配置PIN
默认PIN是123456,默认Admin PIN(PUK)是12345678。CCID模式PIN最多可以包含127个ASCII字符。 它们必须至少为6(PIN)或8(PUK)ASCII字符。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| gpg/card> admin
Admin commands are allowed
gpg/card> passwd
gpg: OpenPGP card no. D2760001240103040006136541830000 detected
1 - change PIN
2 - unblock PIN
3 - change Admin PIN
4 - set the Reset Code
Q - quit
Your selection? 3
PIN changed.
1 - change PIN
2 - unblock PIN
3 - change Admin PIN
4 - set the Reset Code
Q - quit
Your selection? 1
PIN changed.
1 - change PIN
2 - unblock PIN
3 - change Admin PIN
4 - set the Reset Code
Q - quit
Your selection? q
|
设置基本信息
这里设置的字段信息都是可选的:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| gpg/card> name
Cardholder's surname: Xena
Cardholder's given name: Yafa
gpg/card> lang
Language preferences: en
gpg/card> login
Login data (account name): i@yafa.moe
gpg/card> url
URL to retrieve public key: https://www.yafa.moe/yafa.asc
gpg/card> salutation
Salutation (M = Mr., F = Ms., or space): F
gpg/card> forcesig
gpg/card> list
Reader ...........: Yubico YubiKey OTP FIDO CCID
Application ID ...: D2760001240103040006136541830000
Application type .: OpenPGP
Version ..........: 3.4
Manufacturer .....: Yubico
Serial number ....: 13654183
Name of cardholder: Yafa Xena
Language prefs ...: us
Salutation .......: Ms.
URL of public key : https://www.yafa.moe/yafa.asc
Login data .......: [not set]
Signature PIN ....: forced
Key attributes ...: rsa2048 rsa2048 rsa2048
Max. PIN lengths .: 127 127 127
PIN retry counter : 3 0 3
Signature counter : 0
KDF setting ......: off
Signature key ....: [none]
Encryption key....: [none]
Authentication key: [none]
General key info..: [none]
|
传输KEY
重要说明:使用密钥卡将密钥转移到YubiKey只是一种单向操作,不能将yubikey中的密钥再拿出来。 在继续操作之前,请确保已进行了备份:key to card将磁盘上的本地密钥转换为存根,这意味着磁盘上的副本不再可用于传输到后续的安全密钥设备或创建其他密钥。
以前的GPG版本需要在选择密钥之前使用toggle命令。 当前选择的密钥以*表示。 移动键时,一次只能选择一个密钥。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| gpg --edit-key $KEYID
Secret key is available.
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
|
签名
系统将提示你输入主密钥密码和管理员PIN。
选择并传输签名密钥。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| gpg> key 1
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb* rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
gpg> keytocard
Please select where to store the key:
(1) Signature key
(3) Authentication key
Your selection? 1
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb* rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
|
加密
再次输入键1取消选择,再输入2选择下一个密钥:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| gpg> key 1
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
gpg> key 2
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb* rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
gpg> keytocard
Please select where to store the key:
(2) Encryption key
Your selection? 2
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb* rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
|
认证
再次输入2以取消选择,并输入3以选择最后一个密钥:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| gpg> key 2
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
gpg> key 3
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb* rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
gpg> keytocard
Please select where to store the key:
(3) Authentication key
Your selection? 3
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb* rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
|
保存并退出
验证Yubikey工作是否正常
验证子密钥是否已移至YubiKey,如ssb>所示:
1
2
3
4
5
6
7
8
9
| gpg -K
/var/folders/8_/mkr2jpxx1pdgqx7jsnv04k100000gn/T/tmp.UdKeLYEs/pubring.kbx
-------------------------------------------------------------------------
sec rsa4096/0xBE5E83CAC35379C8 2021-03-14 [C]
Key fingerprint = 08A3 150E 30B4 9637 D01C 6C77 BE5E 83CA C353 79C8
uid [ultimate] Yafa Xena (Freedom and responsibility) <i@yafa.moe>
ssb> rsa4096/0xD40C8A853177702B 2021-03-14 [S] [expires: 2022-03-14]
ssb> rsa4096/0x80D9D0834E2A346E 2021-03-14 [E] [expires: 2022-03-14]
ssb> rsa4096/0xD1144013D3F7F320 2021-03-14 [A] [expires: 2022-03-14]
|
yubikey信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| gpg --card-status
Reader ...........: Yubico YubiKey OTP FIDO CCID
Application ID ...: D2760001240103040006136541830000
Application type .: OpenPGP
Version ..........: 3.4
Manufacturer .....: Yubico
Serial number ....: 13654183
Name of cardholder: Yafa Xena
Language prefs ...: us
Salutation .......: Ms.
URL of public key : https://www.yafa.moe/yafa.asc
Login data .......: [not set]
Signature PIN ....: forced
Key attributes ...: rsa4096 rsa4096 rsa4096
Max. PIN lengths .: 127 127 127
PIN retry counter : 3 0 3
Signature counter : 0
KDF setting ......: off
Signature key ....: 1E89 F219 E617 6E21 7946 009A D40C 8A85 3177 702B
created ....: 2021-03-14 05:56:53
Encryption key....: 93AB 2D59 4CAE 483D 43FE 7EAE 80D9 D083 4E2A 346E
created ....: 2021-03-14 05:57:22
Authentication key: CABE A4A2 88F3 6BEC E866 B4A9 D114 4013 D3F7 F320
created ....: 2021-03-14 05:57:39
General key info..: sub rsa4096/0xD40C8A853177702B 2021-03-14 Yafa Xena (Freedom and responsibility) <i@yafa.moe>
sec rsa4096/0xBE5E83CAC35379C8 created: 2021-03-14 expires: never
ssb> rsa4096/0xD40C8A853177702B created: 2021-03-14 expires: 2022-03-14
card-no: 0006 13654183
ssb> rsa4096/0x80D9D0834E2A346E created: 2021-03-14 expires: 2022-03-14
card-no: 0006 13654183
ssb> rsa4096/0xD1144013D3F7F320 created: 2021-03-14 expires: 2022-03-14
card-no: 0006 13654183
|
清理工作
在开始清理工作之前确保这些内容你已经完成了:
- 将加密,签名和身份验证的子密钥保存到yubikey。(对于子密钥,
gpg -K应该显示ssb>) - 记住你设置后的yubikey用户pin和管理员pin
- 记住你的GPG主密钥密码
- 将你主密钥,子密钥和吊销证书的副本保存在加密的卷上(比如说LUKS),并脱机保存。
- 将公钥的副本保存到一个能够轻松访问的位置(我在博客保存了一份,而且还在keyserver保存了一份。)
重要:建议重启机器或者是删除当前电脑上的$GNUPGHOME目录
1
2
3
| cd &&sudo rm -rf $GNUPGHOME
gpg --delete-secret-key $KEYID
unset GNUPGHOME
|
使用
确保你的电脑上有GPG的软件,CCID相关的服务已经启动了。
下载配置文件:
1
2
| cd ~/.gnupg ; wget https://raw.githubusercontent.com/drduh/config/master/gpg.conf
chmod 600 gpg.conf
|
从备份文件中导出公钥:
1
2
| sudo mount /dev/sdf1 /mnt
gpg --import /mnt/0x*txt
|
从keyserver导入GPG 公钥
编辑主密钥,以通过选择和5为其分配最终信任:
重新插入USB然后查看yubikey信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| gpg --card-status
Reader ...........: Yubico YubiKey OTP FIDO CCID
Application ID ...: D2760001240103040006136541830000
Application type .: OpenPGP
Version ..........: 3.4
Manufacturer .....: Yubico
Serial number ....: 13654183
Name of cardholder: Yafa Xena
Language prefs ...: us
Salutation .......: Ms.
URL of public key : https://www.yafa.moe/yafa.asc
Login data .......: [not set]
Signature PIN ....: forced
Key attributes ...: rsa4096 rsa4096 rsa4096
Max. PIN lengths .: 127 127 127
PIN retry counter : 3 0 3
Signature counter : 0
KDF setting ......: off
Signature key ....: 1E89 F219 E617 6E21 7946 009A D40C 8A85 3177 702B
created ....: 2021-03-14 05:56:53
Encryption key....: 93AB 2D59 4CAE 483D 43FE 7EAE 80D9 D083 4E2A 346E
created ....: 2021-03-14 05:57:22
Authentication key: CABE A4A2 88F3 6BEC E866 B4A9 D114 4013 D3F7 F320
created ....: 2021-03-14 05:57:39
General key info..: sub rsa4096/0xD40C8A853177702B 2021-03-14 Yafa Xena (Freedom and responsibility) <i@yafa.moe>
sec rsa4096/0xBE5E83CAC35379C8 created: 2021-03-14 expires: never
ssb> rsa4096/0xD40C8A853177702B created: 2021-03-14 expires: 2022-03-14
card-no: 0006 13654183
ssb> rsa4096/0x80D9D0834E2A346E created: 2021-03-14 expires: 2022-03-14
card-no: 0006 13654183
ssb> rsa4096/0xD1144013D3F7F320 created: 2021-03-14 expires: 2022-03-14
card-no: 0006 13654183
|
我们将信息通过管道给gpg,让其帮我们生成一个加密之后的文件,以此来测试是否工作正常:
1
| echo "test message string" | gpg --encrypt --armor --recipient $KEYID -o encrypted.txt
|
尝试解密信息:
1
2
3
4
5
| gpg --decrypt --armor encrypted.txt
gpg: anonymous recipient; trying secret key 0xF2A3043B78F88E93 ...
gpg: okay, we are the anonymous recipient.
gpg: encrypted with RSA key, ID 0x0000000000000000
test message string
|
签名信息:
1
| echo "test message string" | gpg --armor --clearsign > signed.txt
|
查看签名:
1
2
3
4
5
6
| gpg --verify signed.txt
gpg: Signature made Sun Mar 14 18:44:28 2021 CST
gpg: using RSA key DCFC5352D5FA6FB8457222E643164C130518FCF1
gpg: Good signature from "Yafa Xena (Freedom and responsibility) <i@yafa.moe>" [ultimate]
Primary key fingerprint: 6F10 BB83 80EE B003 58CE 6B04 C696 4DED F01A 4DA0
Subkey fingerprint: DCFC 5352 D5FA 6FB8 4572 22E6 4316 4C13 0518 FCF1
|
这些文件加密解密可能是非常常用的,我们可以为此写一个简单的shell函数用来加密和解密(放到你的shell配置中):
1
2
3
4
5
6
7
8
9
10
11
12
| function reveal {
output=$(echo "${1}" | rev | cut -c16- | rev)
gpg --decrypt --output ${output} "${1}" \
&& echo "${1} -> ${output}" }
function secret { # list preferred id last
output="${HOME}/$(basename ${1}).$(date +%F).enc"
gpg --encrypt --armor \
--output ${output} \
-r 0xC6964DEDF01A4DA0 \
-r i@yafa.moe \
"${1}" && echo "${1} -> ${output}" }
|
使用:
1
2
3
4
5
6
7
| secret IEEE.1364-2005.pdf
reveal ~/IEEE.1364-2005.pdf.2021-03-14.enc
gpg: selecting card failed: Operation not supported by device
gpg: anonymous recipient; trying secret key 0xF2A3043B78F88E93 ...
gpg: okay, we are the anonymous recipient.
gpg: encrypted with RSA key, ID 0x0000000000000000
/Users/yafa/IEEE.1364-2005.pdf.2021-03-14.enc -> /Users/yafa/IEEE.1364-2005.pdf
|
轮转KEY
PGP不提供前向保密性-泄露的密钥可用于解密所有过去的消息。尽管存储在YubiKey上的密钥很难被窃取,但这不是不可能的-例如,可以使用密钥和PIN,或者可以在用于创建密钥的硬件或随机数生成器中发现漏洞。因此,偶尔轮转子密钥是一个好习惯。
子密钥过期后,可以对其进行更新或替换。这两个操作都需要访问脱机主密钥。通过更新子密钥的到期日期来更新子密钥,表明您仍然拥有脱机主密钥,并且更加方便。
另一方面,替换密钥较不方便,但更安全:新的子密钥将无法解密以前的消息,比如说使用SSH进行身份验证等。联系人将需要接收更新的公共密钥,而任何加密的机密都需要解密并重新加密为新的子密钥才能使用。此过程在功能上等效于“丢失” YubiKey,并提供一个新的。但是,你将始终能够使用原始密钥的脱机加密备份来解密以前的消息。
轮换方法都不是上乘方法,它完全取决于身份管理和个人威胁模型的个人理念来决定使用哪个密钥,或者是否使子密钥完全失效。理想情况下,子密钥应是短暂的:每个加密,签名和身份验证事件仅使用一次,但是在实践中,YubiKey并不切实可行或不值得。高级用户可能希望将脱机设备专用于更频繁地轮换密钥并简化配置。
初始化环境
如果想要更新子密钥或者是轮转,差不多就是和生成密钥差不多的流程:
进入livecd环境,安装必要的软件 插入备份密钥的U盘,然后打开LUKS所在的分区:
1
| sudo cryptsetup luksOpen /dev/sdf1 secret
|
创建挂载点并挂载分区:
1
| sudo mount /dev/mapper/secret /mnt/encrypted-storage
|
将主密钥和配置文件导入到临时的工作目录:
1
2
3
| export GNUPGHOME=$(mktemp -d)
gpg --import /mnt/encrypted-storage/tmp.XXX/mastersub.key
cp -v /mnt/encrypted-storage/tmp.XXX/gpg.conf $GNUPGHOME
|
修改主密钥:
1
2
3
4
| export KEYID=0xBE5E83CAC35379C8
gpg --expert --edit-key $KEYID
Secret key is available
[...]
|
续订子密钥
更新子密钥更为简单:无需生成新密钥,将密钥移至YubiKey或更新链接至GPG密钥的任何SSH公共密钥。 需要做的就是更改与公钥关联的到期时间(这需要访问刚刚加载的主密钥),然后导出该公钥并将其导入到希望使用GPG的任何计算机上(例如 与SSH)密钥不同。
要更改所有子键的失效日期,请先选择所有的密钥:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
| gpg --edit-key $KEYID
Secret key is available.
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
gpg> key 1
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb* rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
gpg> key 2
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb* rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb* rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
gpg> key 3
sec rsa4096/0xBE5E83CAC35379C8
created: 2021-03-14 expires: never usage: C
trust: ultimate validity: ultimate
ssb* rsa4096/0xD40C8A853177702B
created: 2021-03-14 expires: 2022-03-14 usage: S
ssb* rsa4096/0x80D9D0834E2A346E
created: 2021-03-14 expires: 2022-03-14 usage: E
ssb* rsa4096/0xD1144013D3F7F320
created: 2021-03-14 expires: 2022-03-14 usage: A
[ultimate] (1). Yafa Xena (Freedom and responsibility) <i@yafa.moe>
|
然后,使用expire命令设置新的到期日期。
1
2
3
4
5
6
7
8
9
| gpg> expire
Changing expiration time for a subkey.
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0)
|
按照这些提示设置新的到期日期,然后保存以保存更改。
接下来,导出公钥:
1
| gpg --export $KEYID > pubkey.gpg
|
将该公钥转移到使用GPG密钥的计算机上,然后使用以下命令导入:
1
| gpg --import pubkey.gpg
|
这将扩展GPG密钥的有效性,并允许将其用于SSH授权。 请注意,实际上不需要更新位于远程服务器上的SSH公共密钥。
旋转KEY
旋转Key需要的操作更多一些。 首先,按照原始步骤生成每个子密钥。 先前的子密钥可以保留或从身份中删除。
通过导出新密钥完成操作:
1
2
| gpg --armor --export-secret-keys $KEYID > $GNUPGHOME/mastersub.key
gpg --armor --export-secret-subkeys $KEYID > $GNUPGHOME/sub.key
|
将新的临时工作目录复制到加密的脱机存储中,该存储仍应挂载:
1
| sudo cp -avi $GNUPGHOME /mnt/encrypted-storage
|
再去查看脱机存储挂载的目录应该有2份不同的主密钥和子密钥的备份:
1
2
| ls /mnt/encrypted-storage
lost+found tmp.lpW6wTr9 tmp.M4PdcQMe
|
卸除挂载然后关闭加密分区:
1
2
| sudo umount /mnt/encrypted-storage
sudo cryptsetup luksClose /dev/mapper/secret
|
导出公钥:
1
2
3
4
| sudo mkdir /mnt/public
sudo mount /dev/mmcblk0p2 /mnt/public
gpg --armor --export $KEYID | sudo tee /mnt/public/$KEYID-$(date +%F).txt
sudo umount /mnt/public
|
断开离线备份的USB设备,然后重新按照之前的步骤将新的密钥转移到yubikey中,以此来替换现有的密钥。之后重新启动计算机或者是删除掉GPGHOME这个临时工作目录。
SSH
这里就是如何用gpg-agent,来达到像是ssh密钥对那样去链接Linux节点。
创建配置文件
首先要下载一个gpg-agent配置文件:
1
2
3
4
5
6
7
8
| cd ~/.gnupg
wget https://raw.githubusercontent.com/drduh/config/master/gpg-agent.conf
grep -ve "^#" gpg-agent.conf
enable-ssh-support
ttyname $GPG_TTY
default-cache-ttl 60
max-cache-ttl 120
pinentry-program /usr/bin/pinentry-curses
|
我这里是Mac环境为此我要修改一下pinentry-program的值
1
| pinentry-program /Applications/MacPorts/pinentry-mac.app/Contents/MacOS/pinentry-mac
|
更换agents
要启动供SSH使用的gpg-agent,请使用gpg-connect-agent/bye或gpgconf --launch gpg-agent命令。
将它们添加到shell rc文件中:
1
2
3
| export GPG_TTY="$(tty)"
export SSH_AUTH_SOCK=$(gpgconf --list-dirs agent-ssh-socket)
gpgconf --launch gpg-agent
|
复制公钥匙
将ssh-add -L的输出复制并粘贴到服务器的authorized_keys文件中:
1
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCzj33cdrl5s1g2AEL3qi/Xro+L6CpcywVuH1Tegw6xHyQO3B1jOS/CtKW5ecmvQBo9GJqP6I4oeu8IjKBRYCkASu28TaVdV2RF1MgpagVCg8TXcdhZ+k7HsKD51TT+jYgTsmZiY0J6pALr9V1vcrtBNIhqbIlF0K4IykCKCICikBzT3qiLPCJgL79s6jiV39VqNOReoALX9uarMkHTeG95Ks+qXcbd/zukqQeWcPjfsc105v8hB7haMENSbpQlGZFiWD5IsU7RQXo6bv941FVBw6M2C5ZMS7aNKacahkRMhdCcNjghdAmyQ2FMGSl+amYMKCBrNzz9CLa1YDr7pRhe3V4y2iSA3YQAtT6eqdxV4+1/ceU8aVhG0no6Vlw3Yclswa5alQ/VGEvkKs2AA4OXhfFubfF1h9UWgORsix6ExojgzZEQoDcSRfT/KJFff0QWI6ySTLcYvyTb9kaKV0ShF6QcsEQdq8KZGB/OaeEmdeVJQF/9dy7Gtq+fKjHzSY/OrU2/ozcl9MN+Rl81yt3hKRhYo/4AQ6LlwqV6o6Y79BjPmx4nd1cU/ZoEayxJkqDCCLfdZOY418df6xthu0qXATJS1nGE40Cinnq0s97e0BOiVPMjmRAwSQQFlQQB+G6KTFAh7Nd1cU6qiuaJ95cYAMoU+7AxTjtOgB6G4tLL8Q== cardno:000613654183
|
这里我拿一台虚拟机进行测试
首先将ssh-add的输出复制到这台虚拟机并更改对应的权限:
1
2
3
4
| mkdir -pv .ssh
vi .ssh/authorized_keys
chmod 640 .ssh/authorized_keys
chmod 700 .ssh/
|
链接这台机器:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
| ssh -vvv root@192.168.56.103
OpenSSH_8.1p1, LibreSSL 2.7.3
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: /etc/ssh/ssh_config line 47: Applying options for *
debug1: Connecting to 192.168.56.103 [192.168.56.103] port 22.
debug1: Connection established.
debug1: identity file /Users/yafa/.ssh/id_rsa type -1
debug1: identity file /Users/yafa/.ssh/id_rsa-cert type -1
debug1: identity file /Users/yafa/.ssh/id_dsa type -1
debug1: identity file /Users/yafa/.ssh/id_dsa-cert type -1
debug1: identity file /Users/yafa/.ssh/id_ecdsa type -1
debug1: identity file /Users/yafa/.ssh/id_ecdsa-cert type -1
debug1: identity file /Users/yafa/.ssh/id_ed25519 type -1
debug1: identity file /Users/yafa/.ssh/id_ed25519-cert type -1
debug1: identity file /Users/yafa/.ssh/id_xmss type -1
debug1: identity file /Users/yafa/.ssh/id_xmss-cert type -1
debug1: Local version string SSH-2.0-OpenSSH_8.1
debug1: Remote protocol version 2.0, remote software version OpenSSH_7.4
debug1: match: OpenSSH_7.4 pat OpenSSH_7.0*,OpenSSH_7.1*,OpenSSH_7.2*,OpenSSH_7.3*,OpenSSH_7.4*,OpenSSH_7.5*,OpenSSH_7.6*,OpenSSH_7.7* compat 0x04000002
debug1: Authenticating to 192.168.56.103:22 as 'root'
debug1: SSH2_MSG_KEXINIT sent
debug1: SSH2_MSG_KEXINIT received
debug1: kex: algorithm: curve25519-sha256
debug1: kex: host key algorithm: ecdsa-sha2-nistp256
debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
debug1: Server host key: ecdsa-sha2-nistp256 SHA256:yDltSSOLjxzYCT7xpi5LPWpQTbPbHhwV+hQHXxpDsYU
debug1: Host '192.168.56.103' is known and matches the ECDSA host key.
debug1: Found key in /Users/yafa/.ssh/known_hosts:4
debug1: rekey out after 134217728 blocks
debug1: SSH2_MSG_NEWKEYS sent
debug1: expecting SSH2_MSG_NEWKEYS
debug1: SSH2_MSG_NEWKEYS received
debug1: rekey in after 134217728 blocks
debug1: Will attempt key: cardno:000613654183 RSA SHA256:HMJRGtFTObD6t0xpTZtFNhmFB6nKIfITVCpEXecGmCA agent
debug1: Will attempt key: /Users/yafa/.ssh/id_rsa
debug1: Will attempt key: /Users/yafa/.ssh/id_dsa
debug1: Will attempt key: /Users/yafa/.ssh/id_ecdsa
debug1: Will attempt key: /Users/yafa/.ssh/id_ed25519
debug1: Will attempt key: /Users/yafa/.ssh/id_xmss
debug1: SSH2_MSG_EXT_INFO received
debug1: kex_input_ext_info: server-sig-algs=<rsa-sha2-256,rsa-sha2-512>
debug1: SSH2_MSG_SERVICE_ACCEPT received
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,password
debug1: Next authentication method: publickey
debug1: Offering public key: cardno:000613654183 RSA SHA256:HMJRGtFTObD6t0xpTZtFNhmFB6nKIfITVCpEXecGmCA agent
debug1: Server accepts key: cardno:000613654183 RSA SHA256:HMJRGtFTObD6t0xpTZtFNhmFB6nKIfITVCpEXecGmCA agent
debug1: Authentication succeeded (publickey).
Authenticated to 192.168.56.103 ([192.168.56.103]:22).
debug1: channel 0: new [client-session]
debug1: Requesting no-more-sessions@openssh.com
debug1: Entering interactive session.
debug1: pledge: network
debug1: client_input_global_request: rtype hostkeys-00@openssh.com want_reply 0
debug1: Sending environment.
debug1: Sending env LC_TERMINAL_VERSION = 3.4.4
debug1: Sending env LC_CTYPE = UTF-8
debug1: Sending env LC_TERMINAL = iTerm2
Last login: Sun Mar 14 19:53:43 2021 from 192.168.56.1
|
在链接的时候会提示你输入yubikey的pin:
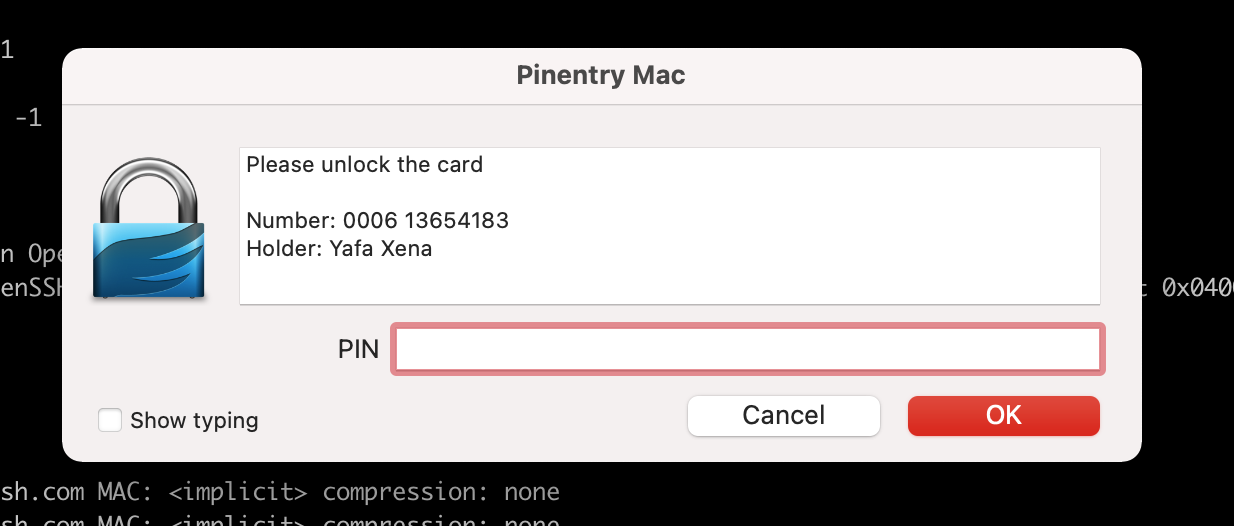
输入正确之后就可以登录到这台机器了~
重置
如果你发现你的yubikey被锁了想要重新设置pin可以运行:
如果你想要重设opengpg的信息可以运行:
常见错误
在重置之后无法将子密钥传输到yubikey上
gpg: KEYTOCARD failed: Unusable secret key
这个可能是长度的问题默认的是rsa 2048的长度 我们需要修改一下:
修改邮件地址
在最初生成邮件地址的时候不是现在所使用的邮件地址,在一段时间的工作之后发现自己有些commit还是使用旧的邮件地址,原来是自己的gpg里面的邮件地址没有修改。。
这里记录一下怎样去修改 gpg的邮件地址
添加一个uid
填写基础的姓名邮箱和注解之后我们来选中新添加的uid
然后信任这个uid
选择 5
接下来取消选择uid(我们新生成的uid)
选择原来的uid
移除原来的uid
最后保存退出
结束语
经过这次折腾经历发现对于安全这块、以及算法部分有相当大的空洞,之后要补习补习这部分的内容了,像是邮件加密之类的功能应该是可以用的,但是我在Thunderbird中配置了一下感觉不是很友好,因为需要将私钥拿出来才能够正常用。。。。
后面看看能否结合yubikey进行端对端的邮件加密
参考链接
